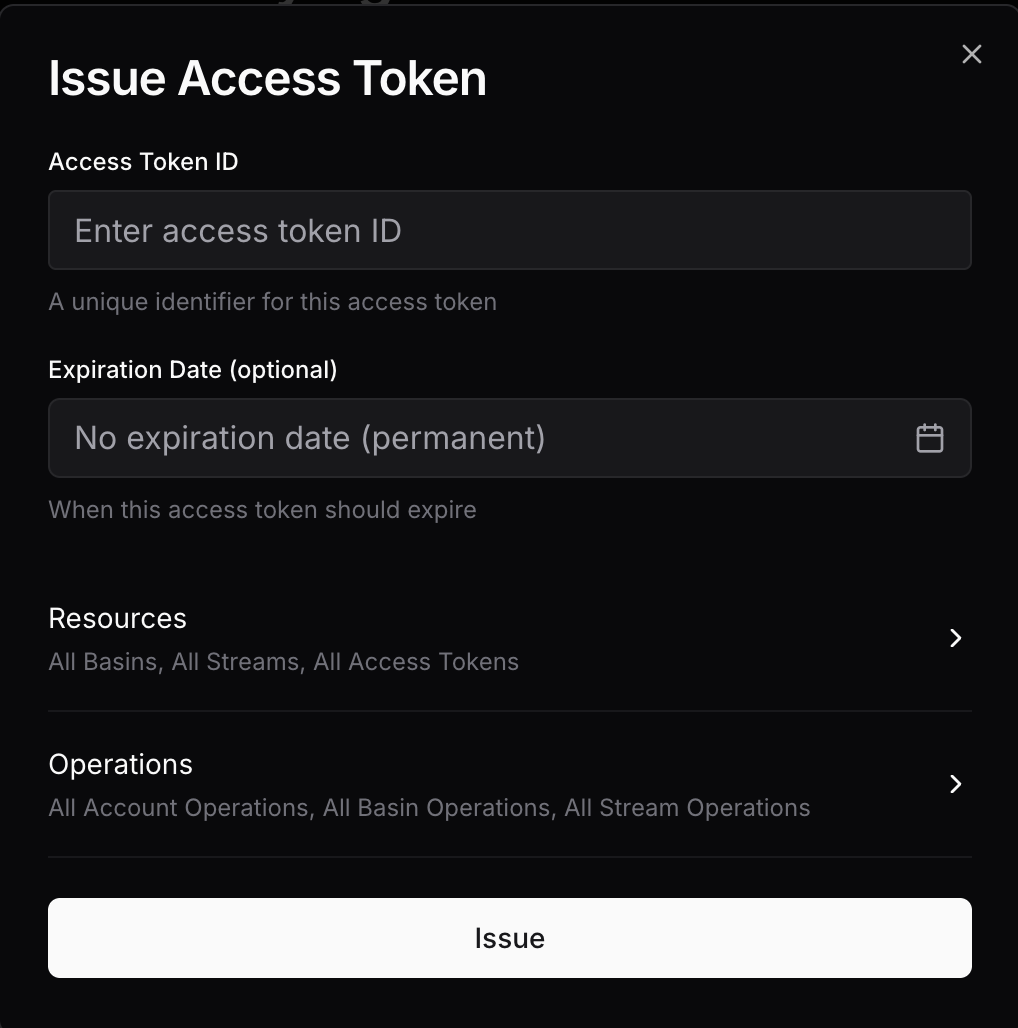
Access tokens are a first-class primitive in S2. Beyond granting administrative access, they support granular scoping — letting you issue tokens with read or write privileges tightly scoped to specific basins, streams, or prefixes. This means your users can interact directly with S2 using tokens that only expose the resources they need.
Tokens are revocable and support time-based expiry. Permanent tokens work well for services; time-bound ones suit ephemeral usage like end-user sessions.
There are 2 ways to list, issue, and revoke access tokens:
Properties
Identifier
Access token IDs must be unique to the account and may be up to 96 bytes in length.
List requests allow prefix filtering, which is handy for namespacing with a delimiter like /. For example, you can name them as user/{user} and service/{service} to easily filter for access tokens for users vs services.
Expiration
An expiry time at which the access token becomes immediately invalid.
This is specified as an RFC 3339 timestamp with the API.
Expiry time of the requestor’s access token will be the default and maximum possible expiry time when issuing a new token.Dashboard access does not have an expiry, so permanent access tokens can be issued from there. However, a limited-expiry access token can be used to only issue new access tokens bounded by its own expiry.
Scope
Resources
Access to the following resources can be scoped:
- Basins
- Streams
- Access tokens
To specify the set of resources for each of these, you can choose either of:
Grant access to all resources with a common prefix:Empty prefix matches all resources (allow all).
Grant access to one specific resource:Empty exact match will not match any resources (deny all).
When configuring access to streams with a prefix, you can also enable auto-prefixing.This acts as a transparent logical namespace within a basin:
- Stream name arguments provided in requests will be automatically prefixed.
- The prefix will be stripped from a response containing a stream name, such as when listing streams.
Operations
There are two complementary ways to authorize operations:
Operation Groups
Individual Operations
Operation groups provide a high-level way to grant read/write access.{
"op_groups": {
"account": { "read": false, "write": false },
"basin": { "read": true, "write": false },
"stream": { "read": true, "write": false }
}
}
For more precise control, explicitly specify the allowed operations:{
"ops": [
"read",
"check-tail"
]
}
Both groups and individual operations may be specified together — the effective permissions are a union.